Remote Access VPN (IPsec) - ASA - part one
Today I implement IPsec remote access VPN on ASA. Please review below diagram:
In first step I implement solution where all traffic will be sent over the tunnel. Later on I try to add more requirements.
As for each VPN configuration I need to implement following elements:
a) Isakmp
crypto isakmp policy 10
auth pre
enr 3des
hash md5
gr 2
crypto isakmp enable outside
b) Ipsec
crypto ipsec ikev1 transform TS esp-3des esp-sha
c) IP pool
ip local pool VPN-POOL 8.8.8.1-8.8.8.8
d) Group policy
group-policy VPN-GP internal
group-policy VPN-GP attributes
vpn-tunnel-prot IPSec
address-pools value VPN-POOL
e) Tunnel group
tunnel-group VPN-ASA type remote-access
tunnel-group VPN-ASA ipsec-attributes
pre-share cisco123
tunnel-group VPN-ASA general-attributes
default-group-policy VPN-GP
f) Crypto map
crypto dynamic-map DMAPA 10 set ikev1 transform TS
crypto dynamic-map DMAPA 10 set reverse-r
crypto map MAPA 10 ipsec-isakmp dynamic DMAPA
crypto map MAPA interface outside
g) username
username cisco password cisco
username cisco attributes
service-type remote-access
I think we can test the configuration. I need to add a new connection entry:
As you notice the group name has to be exactly the same as the tunnel group name. As you may remember from my previous post about IOS, the group name was taken from ‘client configuration group’.
Let’s connect to the VPN server:
On ASA I enabled debugging for ‘ikev1’ and ‘ipsec’:
asa1# debug crypto ipsec 127
asa1# debug crypto ikev1 127
asa1# Dec 08 21:22:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + SA (1) + KE (4) + NONCE (10) + ID (5) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 851
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing SA payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing ke payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing ISA_KE payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing nonce payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing ID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, Received xauth V6 VID
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, Received DPD VID
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, Received Fragmentation VID
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, IKE Peer included IKE fragmentation capability flags: Main Mode: True Aggressive Mode: False
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, Received NAT-Traversal ver 02 VID
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]IP = 192.168.202.221, Received Cisco Unity client VID
Dec 08 21:22:18 [IKEv1]IP = 192.168.202.221, Connection landed on tunnel_group VPN-ASA
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing IKE SA payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, IKE SA Proposal # 1, Transform # 10 acceptable Matches global IKE entry # 1
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing ISAKMP SA payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing ke payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing nonce payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Generating keys for Responder...
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing ID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing hash payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Computing hash for ISAKMP
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing Cisco Unity VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing xauth V6 VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing dpd vid payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing NAT-Traversal VID ver 02 payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing NAT-Discovery payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, computing NAT Discovery hash
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing NAT-Discovery payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, computing NAT Discovery hash
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing Fragmentation VID + extended capabilities payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Send Altiga/Cisco VPN3000/Cisco ASA GW VID
Dec 08 21:22:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=0) with payloads : HDR + SA (1) + KE (4) + NONCE (10) + ID (5) + HASH (8) + VENDOR (13) + VENDOR (13) + VENDOR (13) + VENDOR (13) + NAT-D (130) + NAT-D (130) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 428
Dec 08 21:22:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=0) with payloads : HDR + HASH (8) + NOTIFY (11) + NAT-D (130) + NAT-D (130) + VENDOR (13) + VENDOR (13) + NONE (0) total length : 156
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing hash payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Computing hash for ISAKMP
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing notify payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing NAT-Discovery payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, computing NAT Discovery hash
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing NAT-Discovery payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, computing NAT Discovery hash
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Processing IOS/PIX Vendor ID payload (version: 1.0.0, capabilities: 00000408)
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, processing VID payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Received Cisco Unity client VID
Dec 08 21:22:18 [IKEv1]Group = VPN-ASA, IP = 192.168.202.221, Automatic NAT Detection Status: Remote end is NOT behind a NAT device This end is NOT behind a NAT device
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:22:18 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:22:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=5f76fc84) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 68
And then I type the password:
As you see the connections has been established. On ASA we can see:
asa1# Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=5f76fc84) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 78
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, process_attr(): Enter!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, IP = 192.168.202.221, Processing MODE_CFG Reply attributes.
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: primary DNS = cleared
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: secondary DNS = cleared
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: primary WINS = cleared
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: secondary WINS = cleared
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: IP Compression = disabled
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: Split Tunneling Policy = Disabled
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: Browser Proxy Setting = no-modify
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKEGetUserAttributes: Browser Proxy Bypass Local = disable
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, User (cisco) authenticated.
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=5368b47a) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 60
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=5368b47a) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 56
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, process_attr(): Enter!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Processing cfg ACK attributes
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=9701cf3a) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 185
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, process_attr(): Enter!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Processing cfg Request attributes
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for IPV4 address!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for IPV4 net mask!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for DNS server address!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for WINS server address!
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received unsupported transaction mode attribute: 5
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Banner!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Save PW setting!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Default Domain Name!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Split Tunnel List!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Split DNS!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for PFS setting!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Client Browser Proxy Setting!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for backup ip-sec peer list!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Client Smartcard Removal Disconnect Setting!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for Application Version!
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Client Type: WinNT Client Application Version: 5.0.07.0440
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for FWTYPE!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for DHCP hostname for DDNS is: WIN-NU913FAD068!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, MODE_CFG: Received request for UDP Port!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Obtained IP addr (8.8.8.1) prior to initiating Mode Cfg (XAuth enabled)
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Assigned private IP address 8.8.8.1 to remote user
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Send Client Browser Proxy Attributes!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Browser Proxy set to No-Modify. Browser Proxy data will NOT be included in the mode-cfg reply
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Send Cisco Smartcard Removal Disconnect enable!!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=9701cf3a) with payloads : HDR + HASH (8) + ATTR (14) + NONE (0) total length : 163
Dec 08 21:23:05 [IKEv1 DECODE]IP = 192.168.202.221, IKE Responder starting QM: msg id = 1aacc9c6
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Delay Quick Mode processing, Cert/Trans Exch/RM DSID in progress
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Resume Quick Mode processing, Cert/Trans Exch/RM DSID completed
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, PHASE 1 COMPLETED
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, Keep-alive type for this connection: DPD
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Starting P1 rekey timer: 82080 seconds.
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, sending notify message
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=5ec64eef) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 88
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=1aacc9c6) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NONE (0) total length : 1022
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing SA payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing nonce payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing ID payload
Dec 08 21:23:05 [IKEv1 DECODE]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, ID_IPV4_ADDR ID received
8.8.8.1
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received remote Proxy Host data in ID Payload: Address 8.8.8.1, Protocol 0, Port 0
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing ID payload
Dec 08 21:23:05 [IKEv1 DECODE]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, ID_IPV4_ADDR_SUBNET ID received--0.0.0.0--0.0.0.0
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received local IP Proxy Subnet data in ID Payload: Address 0.0.0.0, Mask 0.0.0.0, Protocol 0, Port 0
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, QM IsRekeyed old sa not found by addr
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKE Remote Peer configured for crypto map: DMAPA
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing IPSec SA payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IPSec SA Proposal # 11, Transform # 1 acceptable Matches global IPSec SA entry # 10
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKE: requesting SPI!
IPSEC: New embryonic SA created @ 0xbc323960,
SCB: 0xBB9BA1B8,
Direction: inbound
SPI : 0xB82FDEE4
Session ID: 0x0000A000
VPIF num : 0x00000002
Tunnel type: ra
Protocol : esp
Lifetime : 240 seconds
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKE got SPI from key engine: SPI = 0xb82fdee4
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, oakley constucting quick mode
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing IPSec SA payload
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Overriding Initiator's IPSec rekeying duration from 2147483 to 28800 seconds
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing IPSec nonce payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing proxy ID
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Transmitting Proxy Id:
Remote host: 8.8.8.1 Protocol 0 Port 0
Local subnet: 0.0.0.0 mask 0.0.0.0 Protocol 0 Port 0
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending RESPONDER LIFETIME notification to Initiator
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:05 [IKEv1 DECODE]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKE Responder sending 2nd QM pkt: msg id = 1aacc9c6
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=1aacc9c6) with payloads : HDR + HASH (8) + SA (1) + NONCE (10) + ID (5) + ID (5) + NOTIFY (11) + NONE (0) total length : 176
Dec 08 21:23:05 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=1aacc9c6) with payloads : HDR + HASH (8) + NONE (0) total length : 48
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, loading all IPSEC SAs
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Generating Quick Mode Key!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, NP encrypt rule look up for crypto map DMAPA 10 matching ACL Unknown: returned cs_id=bc3133c8; rule=00000000
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Generating Quick Mode Key!
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, NP encrypt rule look up for crypto map DMAPA 10 matching ACL Unknown: returned cs_id=bc3133c8; rule=00000000
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Security negotiation complete for User (cisco) Responder, Inbound SPI = 0xb82fdee4, Outbound SPI = 0x1bd57ef6
IPSEC: New embryonic SA created @ 0xbc4371b0,
SCB: 0xBC3160B8,
Direction: outbound
SPI : 0x1BD57EF6
Session ID: 0x0000A000
VPIF num : 0x00000002
Tunnel type: ra
Protocol : esp
Lifetime : 240 seconds
IPSEC: Completed host OBSA update, SPI 0x1BD57EF6
IPSEC: Creating outbound VPN context, SPI 0x1BD57EF6
Flags: 0x00000005
SA : 0xbc4371b0
SPI : 0x1BD57EF6
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x00000000
SCB : 0x0155FBB7
Channel: 0xb62afac0
IPSEC: Completed outbound VPN context, SPI 0x1BD57EF6
VPN handle: 0x0000a014
IPSEC: New outbound encrypt rule, SPI 0x1BD57EF6
Src addr: 0.0.0.0
Src mask: 0.0.0.0
Dst addr: 8.8.8.1
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed outbound encrypt rule, SPI 0x1BD57EF6
Rule ID: 0xbc3157e8
IPSEC: New outbound permit rule, SPI 0x1BD57EF6
Src addr: 192.168.202.219
Src mask: 255.255.255.255
Dst addr: 192.168.202.221
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0x1BD57EF6
Use SPI: true
IPSEC: Completed outbound permit rule, SPI 0x1BD57EF6
Rule ID: 0xbc315d50
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, IKE got a KEY_ADD msg for SA: SPI = 0x1bd57ef6
IPSEC: Completed host IBSA update, SPI 0xB82FDEE4
IPSEC: Creating inbound VPN context, SPI 0xB82FDEE4
Flags: 0x00000006
SA : 0xbc323960
SPI : 0xB82FDEE4
MTU : 0 bytes
VCID : 0x00000000
Peer : 0x0000A014
SCB : 0x015572B7
Channel: 0xb62afac0
IPSEC: Completed inbound VPN context, SPI 0xB82FDEE4
VPN handle: 0x0000c7b4
IPSEC: Updating outbound VPN context 0x0000A014, SPI 0x1BD57EF6
Flags: 0x00000005
SA : 0xbc4371b0
SPI : 0x1BD57EF6
MTU : 1500 bytes
VCID : 0x00000000
Peer : 0x0000C7B4
SCB : 0x0155FBB7
Channel: 0xb62afac0
IPSEC: Completed outbound VPN context, SPI 0x1BD57EF6
VPN handle: 0x0000a014
IPSEC: Completed outbound inner rule, SPI 0x1BD57EF6
Rule ID: 0xbc3157e8
IPSEC: Completed outbound outer SPD rule, SPI 0x1BD57EF6
Rule ID: 0xbc315d50
IPSEC: New inbound tunnel flow rule, SPI 0xB82FDEE4
Src addr: 8.8.8.1
Src mask: 255.255.255.255
Dst addr: 0.0.0.0
Dst mask: 0.0.0.0
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 0
Use protocol: false
SPI: 0x00000000
Use SPI: false
IPSEC: Completed inbound tunnel flow rule, SPI 0xB82FDEE4
Rule ID: 0xbc43c1f8
IPSEC: New inbound decrypt rule, SPI 0xB82FDEE4
Src addr: 192.168.202.221
Src mask: 255.255.255.255
Dst addr: 192.168.202.219
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0xB82FDEE4
Use SPI: true
IPSEC: Completed inbound decrypt rule, SPI 0xB82FDEE4
Rule ID: 0xbc43c290
IPSEC: New inbound permit rule, SPI 0xB82FDEE4
Src addr: 192.168.202.221
Src mask: 255.255.255.255
Dst addr: 192.168.202.219
Dst mask: 255.255.255.255
Src ports
Upper: 0
Lower: 0
Op : ignore
Dst ports
Upper: 0
Lower: 0
Op : ignore
Protocol: 50
Use protocol: true
SPI: 0xB82FDEE4
Use SPI: true
IPSEC: Completed inbound permit rule, SPI 0xB82FDEE4
Rule ID: 0xbc3162e8
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Pitcher: received KEY_UPDATE, spi 0xb82fdee4
Dec 08 21:23:05 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Starting P2 rekey timer: 27360 seconds.
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Adding static route for client address: 8.8.8.1
Dec 08 21:23:05 [IKEv1]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, PHASE 2 COMPLETED (msgid=1aacc9c6)
Dec 08 21:23:16 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=48bc649) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec065e)
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec065e)
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:16 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:16 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=a9b0b86f) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:26 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=767ffd9c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec065f)
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec065f)
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:26 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:26 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=f6d87865) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:37 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=a81f1456) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0660)
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0660)
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:37 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:37 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=d7f4b665) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:47 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=6fb0be4e) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0661)
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0661)
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:47 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:47 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=2b94891b) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:57 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=455566e) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0662)
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0662)
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:23:57 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:23:57 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=14ae9da1) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:07 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=dacfbea9) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0663)
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0663)
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:07 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:07 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=55816a2f) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=f6dde082) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0664)
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0664)
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:18 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:18 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=48401ac5) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:28 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=a03ffb4f) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0665)
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0665)
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:28 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:28 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=82487e3e) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:38 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=1704039a) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0666)
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0666)
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:38 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:38 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=1de6a54c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:49 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=7679c777) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0667)
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0667)
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:49 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:49 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=b3121882) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:59 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=73ee485c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0668)
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0668)
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:24:59 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:24:59 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=e974054c) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:25:09 [IKEv1]IP = 192.168.202.221, IKE_DECODE RECEIVED Message (msgid=ac64c8b9) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing hash payload
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, processing notify payload
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Received keep-alive of type DPD R-U-THERE (seq number 0x47ec0669)
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, Sending keep-alive of type DPD R-U-THERE-ACK (seq number 0x47ec0669)
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing blank hash payload
Dec 08 21:25:09 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.221, constructing qm hash payload
Dec 08 21:25:09 [IKEv1]IP = 192.168.202.221, IKE_DECODE SENDING Message (msgid=90e48a40) with payloads : HDR + HASH (8) + NOTIFY (11) + NONE (0) total length : 80
I check now isakmp and ipsec sa:
asa1# sh crypto ikev1 sa detail
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 192.168.202.221
Type : user Role : responder
Rekey : no State : AM_ACTIVE
Encrypt : 3des Hash : MD5
Auth : preshared Lifetime: 86400
Lifetime Remaining: 86017
asa1# sh crypto ipsec sa
interface: outside
Crypto map tag: DMAPA, seq num: 10, local addr: 192.168.202.219
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (8.8.8.1/255.255.255.255/0/0)
current_peer: 192.168.202.221, username: cisco
dynamic allocated peer ip: 8.8.8.1
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 200, #pkts decrypt: 200, #pkts verify: 200
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.202.219/0, remote crypto endpt.: 192.168.202.221/0
path mtu 1500, ipsec overhead 58, media mtu 1500
current outbound spi: 1BD57EF6
current inbound spi : B82FDEE4
inbound esp sas:
spi: 0xB82FDEE4 (3090144996)
transform: esp-3des esp-md5-hmac no compression
in use settings ={RA, Tunnel, }
slot: 0, conn_id: 40960, crypto-map: DMAPA
sa timing: remaining key lifetime (sec): 28409
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0x1BD57EF6 (466976502)
transform: esp-3des esp-md5-hmac no compression
in use settings ={RA, Tunnel, }
slot: 0, conn_id: 40960, crypto-map: DMAPA
sa timing: remaining key lifetime (sec): 28409
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
asa1#
Let’s test connection between VPN client and the router behind the VPN server:
As you see I can ping all interfaces and from statistics I see the ping packets are encrypted and decrypted correctly.
asa1# sh crypto ipsec sa | i pkts
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 275, #pkts decrypt: 275, #pkts verify: 275
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0
asa1#
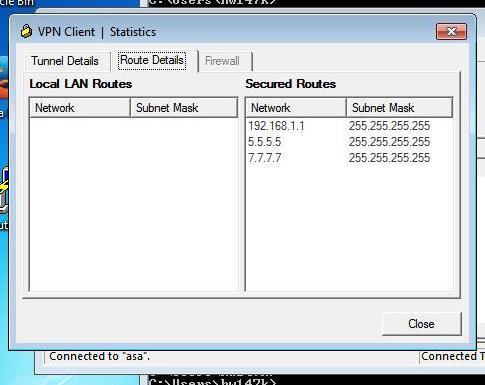
From the ‘Route Details’ tab you can learn there is no split tunneling and it means whole traffic from client machine is sent over the tunnel:
Now I need to change my requirement a bit and traffic to IP 9.9.9.9 should be sent over the Internet. I have to add access list on ASA and then add access list to define the traffic for split tunneling.
asa1(config)# access-list OUT extended permit icmp any host 9.9.9.9
asa1(config)# access-group OUT in interface outside
As you see above without the vpn I can ping 9.9.9.9.
One of the method to enable the split tunneling is to tunnel only specified subnets/IPs:
access-list SPLIT-TUN standard permit host 5.5.5.5
access-list SPLIT-TUN standard permit host 7.7.7.7
access-list SPLIT-TUN standard permit host 192.168.1.1
group-policy VPN-GP attributes
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT-TUN
As you see now only specified netoworks/IPs can be sent over the tunnel:
When I ping host 9.9.9.9, which is not on the list, I see no packets is sent over the tunnel:
In next post I will add more requirements and I will try to analyze ikev1 steps.
Hint: if you can’t remember all steps, there is one command you like it:
asa1(config)# vpnsetup ?
configure mode commands/options:
ipsec-remote-access Display IPSec Remote Access Configuration Commands
l2tp-remote-access Display L2TP/IPSec Configuration Commands
site-to-site Display IPSec Site-to-Site Configuration Commands
ssl-remote-access Display SSL Remote Access Configuration Commands
asa1(config)#
asa1(config)# vpnsetup ipsec-remote-access steps
Steps to configure a remote access IKE/IPSec connection with examples:
1. Configure Interfaces
interface GigabitEthernet0/0
ip address 10.10.4.200 255.255.255.0
nameif outside
no shutdown
interface GigabitEthernet0/1
ip address 192.168.0.20 255.255.255.0
nameif inside
no shutdown
2. Configure ISAKMP policy
crypto isakmp policy 65535
authentication pre-share
encryption aes
hash sha
3. Setup an address pool
ip local pool client-pool 192.168.1.1-192.168.1.254
4. Configure authentication method
aaa-server MyRadius protocol radius
aaa-server MyRadius host 192.168.0.254
key $ecretK3y
5. Define tunnel group
tunnel-group client type remote-access
tunnel-group client general-attributes
address-pool client-pool
authentication-server-group MyRadius
tunnel-group client ipsec-attributes
pre-shared-key VpnUs3rsP@ss
6. Setup ipsec parameters
crypto ipsec transform-set myset esp-aes esp-sha-hmac
7. Setup dynamic crypto map
crypto dynamic-map dynmap 1 set transform-set myset
crypto dynamic-map dynmap 1 set reverse-route
8. Create crypto map entry and associate dynamic map with it
crypto map mymap 65535 ipsec-isakmp dynamic dynmap
9. Attach crypto map to interface
crypto map mymap interface outside
10. Enable isakmp on interface
crypto isakmp enable outside
asa1(config)#
The only one problem is that it is wasn’t updated to ikev1/ikev2 and for example ‘ipsec transform-set’ is not valid anymore. I think the changes are so small you can easily adopt them by yourself.