Remote Access VPN (IPsec) - ASA - part two
In my previous post I configured the remote access IPsec VPN on ASA and today I’d like to change some settings. I added one more router which will play a role of a www server.
In my last scenario all traffic was sent over the tunnel:
and today I need to separate the traffic in two categories: first one - protected and it should be sent over the tunnel; second one - can be sent over the Internet. On my updated network diagram you can see R16 /192.168.202.222/. Assume it is a www server, and we should be able to access it not via the VPN tunnel. The traffic to servers behind the ASA have to be protected.
First I add a new access list:
asa1(config)# access-list SPLIT-TUN standard permit host 192.168.202.222
next, I need to change group policy settings:
group-policy VPN-GP attributes
split-tunnel-policy excludespecified
split-tunnel-network-list value SPLIT-TUN
I try now to establish the VPN connection.
On the ASA I see the access list associated with split tunneling and split tunneling policy:
Dec 10 07:27:56 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.232, IKEGetUserAttributes: split tunneling list = SPLIT-TUN
Dec 10 07:27:56 [IKEv1 DEBUG]Group = VPN-ASA, Username = cisco, IP = 192.168.202.232, IKEGetUserAttributes: Split Tunneling Policy = Local Lan
Now I should be able to send traffic to the host 192.168.202.222 but there is one problem:
When we look at the second tab you can notice that one (mandatory !!!) parameter is not enabled (Local LAN: disabled):
Let’s fix it:
and connect once again:
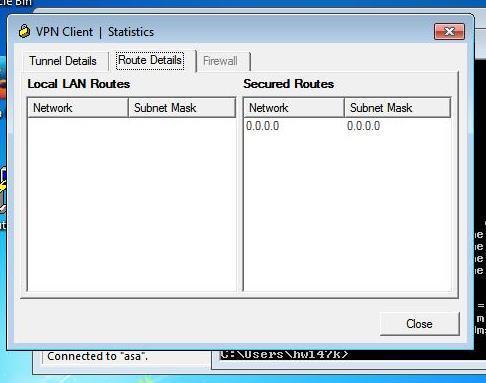
As you see now this one IP address is excluded from encryption domain.
On the client side you can also find following logs:
Let’s send some traffic to check if it works as expected:
Now I test if I can ping hosts behind the ASA:
So, everything works fine.
I’d like to mention about one thing. Assume the host 9.9.9.9 is a www server in DMZ and you don’t need to protect the traffic between client and this server. You can add this IP to the access list (SPLIT-TUN) and the traffic will not be encrypted:
asa1(config)# access-list SPLIT-TUN standard permit host 9.9.9.9
now let’s send some traffic to the host 9.9.9.9:
As you see everything is working as expected. You can exclude the traffic from the VPN tunnel which is directed to host in different location but also to the LAN just behind the VPN server.